Document and track personal data breaches
This guide will help you identify personal data breaches that affect your organization and manage them when there's a risk.
In this article
Browse through the data breach report form
What is a data breach?
Article 4.12 of the GDPR defines a personal data breach as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data transmitted, stored, or otherwise processed;
Browse through the data breach form
To access and perform actions on the Personal data breach page, you need Access to Data Breach page permission.
There are five tabs on each data breach form: Description, Risk assessment, Actions take, Actions, and Documents.
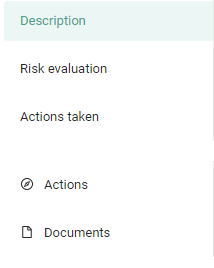
- Use Description and Risk assessment to fill in its information.
- Use Actions taken to know if you need to notify someone.
- Use Actions and Documents to manage and monitor your data breach.
Add a new data breach
With the GDPR software, add a data breach that occurred in your entity in a few clicks. Go to Personal data breach ![]() and click Add a data breach.
and click Add a data breach.
To save time and describe the data breach effortlessly, indicate information required by the supervisory authority. Every field is saved automatically. So your work is safe if you don't finish the completion of the form.
This topic will help you complete the sections under Description.
Identification
Under Identification, describe the context of the data breach as precisely as possible. The fields to complete help you identify when, why, and how the data breach occurred.
Don't forget to indicate when you detected the data breach. Indeed, if the data breach constitutes a risk, you should notify the supervisory authority 72 hours after acknowledging it. After this period, you need to justify your delay.

Categories of data and data subjects
Tell the categories of personal data and data subjects affected by a data breach. It helps you assess the importance of the impact. Indeed, the more sensitive the data category, the more significant the impact.
Please note that the categories of data subjects suggested are only those listed in the repository. Since the data breach is associated with processing, you can't create a category of data subjects at this step.

Processing
You can specify the processing affected by a data breach. Use this link to consult data subject categories and data categories potentially impacted by a data breach.

Assess risk
Now that you have completed the description of the data breach, it is time to assess it. The goals are to indicate its likely consequences and determine whether there's a risk and its importance.
Data breaches are different. That is why, for each assessment, we recommend notifying or not the supervisory authority and data subjects affected by the data breach.
Learn more about assessing a breach.

Manage risk
You also can check and track actions to take on data breaches that present risk.
Thus, from the Actions Taken tab, you can:
- Describe security measures considered or taken to prevent this type of data breach from happening again.
- Know who to notify of the data breach.
- Check the deadline to notify them.
- Indicate if and when you have notified the supervisory authority and the persons concerned.
If you have missed the deadline, justify your delay in the Comments field.
Schedule actions
There is a task scheduler in each data breach form. It is optional, but it helps you organize the management of the data breach and facilitates collaboration between colleagues.

To add an action, click Actions, then Add.
You will be able to:
- Assign a priority level to actions.
- Track its progress.
- Assign them to one or more colleagues.
- Schedule a due date for it.
Import files
The Documents tab allows you to complete the violation with contextual documents. Imported files can be incident reports, complaint filings, notifications to the control authority in PDF format, or a copy of the email sent to data subjects affected by the data breach.
You can also find files imported in the data breach form in the document management module, Accountability.